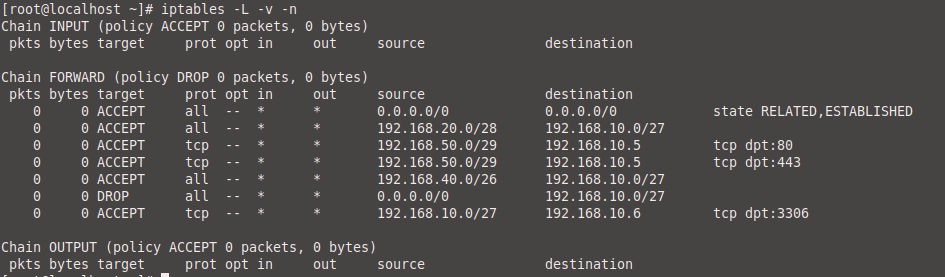
Since we want to control everything that reaches the DMZ, we put:
-
iptables -P FORWARD DROP
![]()
This means that no VLAN can talk to the DMZ unless we specifically tell it to.
Rules consistent with the policy
1. Administration can access the entire DMZ (for server management)
-
iptables -A FORWARD -s 192.168.20.0/28 -d 192.168.10.0/27 -j ACCEPT
![]()
2. Guests can only access the WEB server (HTTP and HTTPS)
-
iptables -A FORWARD -s 192.168.50.0/29 -d 192.168.10.5 -p tcp --dport 80 -j ACCEPT
-
iptables -A FORWARD -s 192.168.50.0/29 -d 192.168.10.5 -p tcp --dport 443 -j ACCEPT
![]()
3. Backup can access the servers to make copies
-
iptables -A FORWARD -s 192.168.40.0/26 -d 192.168.10.0/27 -j ACCEPT
![]()
4. Production can access the BBDD
-
iptables -A FORWARD -s 192.168.10.0/27 -d 192.168.10.6 -p tcp --dport 3306 -j ACCEPT
![]()