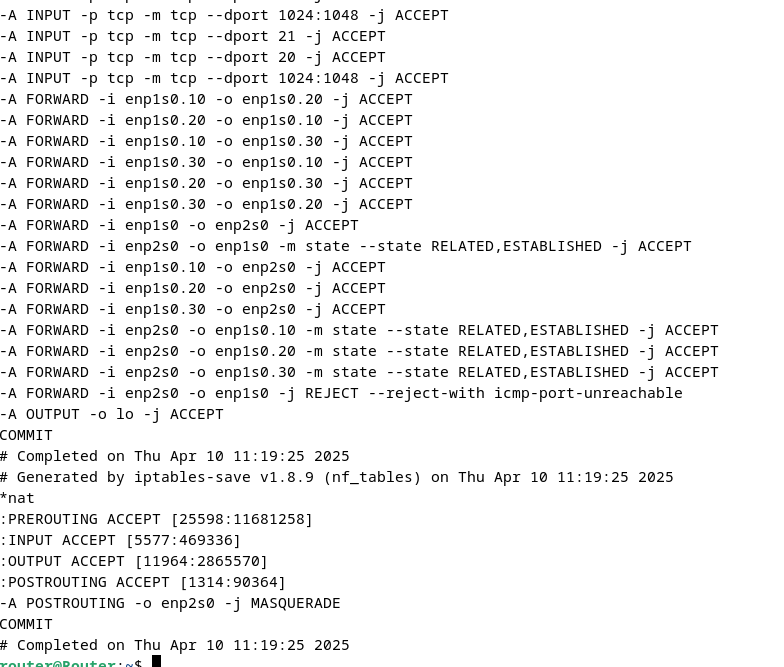
🧱 Filter Section
This part manages traffic control rules in the INPUT, FORWARD, and OUTPUT chains, which regulate which packets are allowed to enter, leave, or be forwarded through the firewall.
🔧 Default Policies:
INPUT ACCEPT→ Accepts all incoming traffic. This means any packet not matching a specific rule will be allowed.FORWARD ACCEPT→ Accepts all forwarding traffic between network interfaces.OUTPUT ACCEPT→ Allows all outgoing traffic without restrictions.
🔐 Input Rules (INPUT)
These rules control incoming traffic to the device (router). Some specific examples:
-A INPUT -i lo -j ACCEPT
→ Allows all traffic on the loopback interface (lo), necessary for local system operations.
-A INPUT -p tcp -m tcp --dport 21 -j ACCEPT
→ Allows FTP traffic on port 21.
-A INPUT -p tcp -m tcp --dport 20 -j ACCEPT
→ Allows FTP-DATA traffic on port 20.
-A INPUT -p tcp -m tcp --dport 1024:1048 -j ACCEPT
→ Allows connections on dynamic ports 1024-1048.
🔁 Forwarding Rules (FORWARD)
This configures the traffic passing through the router, i.e., packets sent between network interfaces:
-A FORWARD -i enp1s0.10 -o enp1s0.20 -j ACCEPT
→ Allows traffic between subnets enp1s0.10 and enp1s0.20.
-A FORWARD -i enp1s0 -o enp2s0 -j ACCEPT
→ Allows traffic from enp1s0 to enp2s0 (likely the Internet-facing interface).
-A FORWARD -i enp2s0 -o enp1s0 -m state --state RELATED,ESTABLISHED -j ACCEPT
→ Allows response packets from the Internet back to the internal network, ensuring only return traffic is allowed.
-A FORWARD -i enp2s0 -o enp1s0 -j REJECT --reject-with icmp-port-unreachable
→ Blocks unauthorized traffic from the Internet to the internal network.
✅ Key points:
The internal network is protected by only allowing return traffic.
Communication between VLANs (
enp1s0.10,enp1s0.20,enp1s0.30) is allowed.Direct access from the Internet to the internal network is blocked — a good security practice.
📤 Output Rules (OUTPUT)
-A OUTPUT -o lo -j ACCEPT
→ Allows traffic on the loopback interface (lo), important for internal system processes.
🌐 NAT Section
This part configures Network Address Translation, necessary for internal devices to access the Internet.
🔁 MASQUERADE Rule
-A POSTROUTING -o enp2s0 -j MASQUERADE
What does this rule do?
This rule hides the private IP addresses of internal devices and replaces them with the router’s public IP when going out via enp2s0. It’s essential to enable Internet browsing for internal devices.
✅ Function Summary
Traffic Filtering: Essential traffic is allowed within the internal network, while direct access from the Internet is blocked.
VLAN Communication: Traffic is allowed between internal subnets (
enp1s0.10,enp1s0.20,enp1s0.30).Router Protection: Only return traffic from the Internet is allowed; direct access to the internal network is blocked.
Address Translation (NAT): MASQUERADE is used to allow internal devices to browse the Internet.
